Deep Analysis of Miden: A High-Performance Zero-Knowledge Virtual Machine Architecture Based on STARK
1. Introduction
With the continuous deepening of blockchain applications at scale, privacy protection and scalability have become core challenges urgently awaiting solutions across the industry. The emergence of Zero-Knowledge Proof (ZKP) technology provides a feasible path to address both simultaneously. As Ethereum co-founder Vitalik Buterin stated, “Highly efficient zero-knowledge proofs (ZK-SNARKs) can reveal enough information to prove our credibility while protecting our identity privacy” . In a recent blog post titled 《Why I support privacy》, he further pointed out: “Supporting privacy for everyone, and making the necessary tools open-source, universal, reliable, and secure, is one of the important challenges of our time.”
Privacy is not only a personal right but also the cornerstone of decentralization and censorship resistance. Meanwhile, ZK-Rollup, as a leader in Layer 2 solutions, is rapidly evolving, from early solutions focused on scalability like zkSync and Optimism, all the way to today’s zkEVM, constantly seeking balance between performance and compatibility. Miden has emerged against this background as a brand-new solution—it not only leverages the efficiency of STARK (Scalable Transparent ARguments of Knowledge: a zero-knowledge proof technology that allows others to quickly and confidently verify results without revealing computational details, with strong security, quantum resistance, and no need for any “trusted third party”. The efficiency of the proof system further pushes execution and state to the user side, redefining the concept of “composable privacy Rollup”.
2. Introduction to Miden

Source: https://x.com/0xMiden
Miden was incubated by Polygon Labs and became the independent 0xMiden project in spring 2025, positioning itself as an “Edge Blockchain”. Unlike traditional Rollups that require all transactions to be executed on-chain, Miden migrates most of the computation and proof generation processes to client devices, then submits compact STARK proofs to the network for verification. Polygon’s official blog states: “Miden will continue to evolve into a zero-knowledge driven ‘edge’ blockchain that moves execution and state to the client. Unlike traditional chains such as Sui, Aptos, and Solana, Miden unlocks a new design space for deploying scalable, privacy-friendly applications. After pushing state and execution down to user devices, developers can build powerful systems with complex logic and hybrid public-private states while maintaining user confidentiality and compliance.”

Source: Polygon Official Blog
Miden’s core advantages are reflected in the following aspects:
- High throughput and parallel execution: Inspired by the Actor model, each account (Actor) independently executes and generates proofs, eliminating global lock contention and greatly improving parallelism and throughput.
- Privacy-first with optional disclosure: Default private ledger only stores state commitments, with the option to selectively disclose specific transactions or contract calls when necessary, enabling flexible privacy strategies.
- Client-side local proving: Leveraging STARK’s transparency and efficiency, client devices can complete proof generation for complex transactions within 1-2 seconds. As of May 6, 2025 Beijing time, the cost of generating common proofs on mainstream MacBook Pro is approximately 90K cycles.
- Compatible with Ethereum security: Miden Rollup’s AggLayer is tightly integrated with the Ethereum mainnet, inheriting its strong security guarantees and decentralized characteristics.
Specifically, the Polygon Miden website states: “With Polygon Miden, developers can build novel high-throughput, privacy-friendly applications spanning payments, DeFi, digital assets, and gaming, with applications and users securely anchored to Ethereum and AggLayer” . To date, Miden has completed open-sourcing its VM, released its developer SDK, and entered the Alpha testnet v6 phase, drawing ever closer to its mainnet launch target in the fourth quarter of 2025.
In summary, by combining “client-side execution + ZK proofs + edge architecture,” Miden not only provides a new paradigm for quantifiable privacy and unlimited scalability but also lays the technological foundation for the next generation of Web3 infrastructure. Next, we will delve deeper into its VM architecture and proof system.
3. Detailed Analysis of Miden VM Architecture
Miden VM is a Turing-complete virtual machine specifically designed for efficient zero-knowledge proofs, with its core objective being the local execution of smart contract logic on client devices and generation of STARK proofs that can be quickly verified on-chain. The following four sub-sections provide an in-depth analysis of its architectural composition and execution process.
3.1 Stack-based Virtual Machine and Instruction Set
Stack-based Execution Model
Miden VM adopts a stack machine architecture, where all instruction inputs and outputs are processed through an operation stack. This design greatly simplifies state representation during proof generation, as only stack read/write operations need to be recorded, without maintaining complex register states.RISC-like Minimal Instruction Set
The virtual machine instruction set is kept deliberately simple—similar to a Reduced Instruction Set Computer (RISC)—to minimize the number of provable constraints. For example, arithmetic operations, logical operations, stack operations, and control flow instructions are broken down into the most basic micro-ops, with each instruction mapped to finite field arithmetic relations during proof generation. Miden VM efficiently transforms the execution of each instruction into algebraic constraints, generating and verifying them through STARK, with proof size loosely coupled to program complexity.
3.2 Program Memory Organization
During execution, the program state in Miden VM is distributed across the following logical segments:
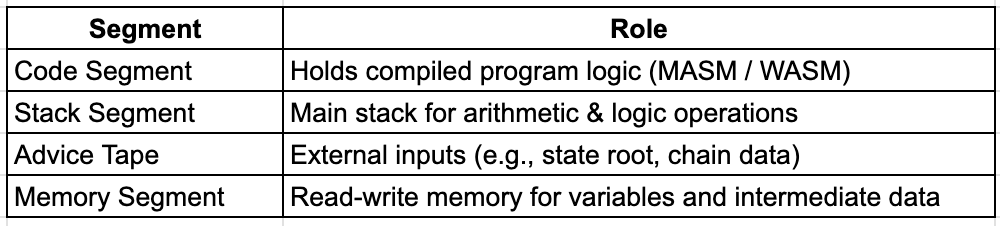
Miden VM Memory Segment Responsibility Table (Source: Gate Learn Creator Max)
This multi-segment memory model not only facilitates different data access patterns but also helps independently constrain each segment during proof construction, optimizing lookups and parallelism.
3.3 Execution Flow and Proof Generation

Miden VM Architecture Diagram (Source: Gate Learn Creator Max)
Loading and Initialization
The client loads contract bytecode into the Code Segment, prepares the execution context, and obtains necessary Advice Tape inputs from the blockchain or side channel; it also loads the initial state commitment of an account or note.Trace Table Construction
During execution, the VM sequentially records a “Trace Table”—a multi-column table where each column represents the evolution of memory segments or stack top positions over time.AIR Transformation
The Trace Table is converted into an Algebraic Intermediate Representation (AIR), encoding all consistency conditions for VM behavior (such as stack pointer increments/decrements, instruction semantics) as polynomial constraints.STARK Proof
The Prover generates a STARK proof for the AIR. Due to STARK’s transparency (no trusted setup required) and efficiency, the client only needs O(N log N) time to process thousands of instruction-level Traces.Verifier Validation
The verifier only needs to check submitted polynomial evaluations and low-dimensional sampling, with complexity at the polynomial level of the proof size, typically completing within tens of milliseconds, greatly improving on-chain throughput.
The entire execution and proof generation process takes approximately 1-2 seconds (about 90K VM cycles) on the Miden client, while on-chain verification is even faster, enabling large-scale parallel transaction validation.
3.4 Parallelism and Composability
Actor Model
Miden VM treats each account (or note) as an independent Actor, with execution and state updates completely decoupled. This allows multiple transaction scripts to execute in parallel on the client, generate proofs in parallel, and then be submitted in batches for network aggregated validation. The Actor model combined with zero-knowledge proofs lets users prove state transitions locally, which are then aggregated in parallel by the network, significantly increasing throughput.Composable Scripts
Through Foreign Procedure Invocation (FPI), one contract script can call another contract’s “read-only” procedure without interrupting the local proof process. FPI essentially incorporates cross-contract read-only call state operations into the same Trace Table, achieving efficient composition.
3.5 Simple Explanation: What is Miden VM Like?
You can imagine Miden VM as a “privacy computing micro-factory” that executes tasks locally on your smartphone and produces an officially certified “work record” that can be sent to the main network for verification.
Example:
Suppose you’re using an on-chain RPG game where you buy a piece of land and then build a castle using game coins.
In traditional smart contracts: All your operations (position, fund flow, building actions) must be executed on-chain, with information completely public, both wasting block space and compromising privacy.
Using Miden VM:
- All logic—“Do I have enough coins? Am I in the correct position? Do I comply with building rules?”—is executed locally on your phone;
- Then Miden VM generates a mathematical proof (STARK proof) on your phone, telling the network: “This user definitely followed the rules”;
- The blockchain doesn’t need to know how you built it, it only verifies the proof is correct and updates the state.
The benefits of this design are:
- The network doesn’t need to execute every transaction, only verify proofs, saving resources;
- User operations can remain completely private, with selective disclosure only when needed;
- Multiple players can execute their own logic and generate their own proofs simultaneously, with extremely high parallelism, without competing for on-chain resources.
In conclusion, the key to Miden VM’s architecture lies in simplified provable instructions, multi-segment memory separation, efficient Air→STARK pipeline, and the Actor parallel model, ensuring that complex logic can be easily expressed on client devices while proof verification can be completed on-chain at extremely low cost, providing a solid foundation for the next generation of high-performance, privacy-friendly ZK-Rollup applications.
4. Miden’s Proof System: STARK-Powered Verifiable Execution Engine

Miden proof system diagram (Source: Gate Learn creator Max)
In Miden, zero-knowledge proofs aren’t just an “add-on module,” but the core operating mechanism of the entire protocol. Miden is built on the STARK (Scalable Transparent ARguments of Knowledge) system, designed from the ground up for “local execution + zero-knowledge proofs.” This section will deeply analyze Miden’s proof process and its underlying mathematical mechanisms, explaining why STARK is its preferred choice.
4.1 Why Choose STARK Instead of SNARK?
Compared to SNARK technology widely used in projects like zkEVM, Miden chose STARK technology for three key reasons:
No Trusted Setup Required (Transparent)
STARK uses hash functions (such as Rescue, Blake3, etc.) rather than elliptic curve cryptography, eliminating dependence on trusted initial parameters. This removes the centralization risks that come with “multi-party computation (MPC) trusted setup failures.”Quantum Attack Resistance
STARK is based on hash security, making it more robust against future quantum computing threats.Fast Proof Generation, Efficient Verification
Although STARK proofs are slightly larger than SNARK proofs, they verify faster, making them more suitable for large-scale parallel verification on-chain.
The research team at Polygon Labs states:
“Miden chose STARK not to be compatible with old paradigms, but to design an entirely new system that maximizes scalability and security.”
4.2 Trace Table and Execution Trajectory
In traditional computing, we can record every step of program execution, such as each variable assignment or function call. In Miden VM, these operations are transformed into an execution trace—a table called the Trace Table that contains snapshots of the program’s state at each step in the time dimension.
Each column in the Trace Table represents the evolution of a register, memory unit, or stack value;
Each row represents a moment (cycle) in the program’s execution.
For example:

Every Miden instruction can be precisely recorded and converted into constraints for the next stage of proof construction.
4.3 AIR (Algebraic Intermediate Representation)
After constructing the Trace Table, the next step is converting it to AIR (Algebraic Intermediate Representation). This is a method of representing program semantics as polynomial constraints, with core ideas including:
- Each rule, such as “the stack top after addition equals the sum of two numbers,” can be expressed as: “stack[0]_next = stack[0]_curr + stack[1]_curr”
- All rules are verified in a finite field, ensuring the STARK system can efficiently generate proofs.
- Low Degree Extension (LDE) technology is used to extend discrete data into continuous functions, making deceptive modifications detectable through probabilistic testing.
Through AIR, Miden can encode the claim “the execution is valid” as a mathematically verifiable statement.
4.4 STARK Proof Process
The complete STARK proof generation includes the following steps:
- Prover builds execution trace: Generates a Trace Table based on the smart contract logic executed locally by the user;
- Conversion to AIR system: Maps each instruction to algebraic constraints;
- Low-degree extension and commitment: Commits to the extended data through mechanisms like Merkle Trees;
- FRI protocol: Verifies the low-degree property of polynomials, ensuring the trace is valid;
- Proof output: Generates a proof of approximately 30-100KB, which the user submits to the network.
This entire process is completed on the client side, typically taking only 1-2 seconds, and can even run on mobile devices (or be delegated to external prover services if performance is insufficient).
4.5 On-Chain Verification and State Updates
Miden’s on-chain Verifier contract (inherited from Ethereum) performs the following operations on received STARK proofs:
- Quickly validates whether the AIR holds (through sampling verification);
- Checks if public inputs (such as state commitments, block height) match;
- Updates the global state (such as account storage trees, Nullifiers);
- Registers new states or consumes states of notes.
Thanks to STARK’s transparency and parallelism, the Verifier can simultaneously verify proofs of thousands of transactions, greatly increasing throughput and reducing on-chain load.
4.6 Simple Explanation: Miden’s STARK Proof System is Like a “Mathematical Receipt”
You can think of Miden’s zero-knowledge proof process as a “paperless banking transaction”:
Metaphorical scenario:
Imagine you’re making a bank transfer, but you don’t want the bank to know how much money you transferred, to whom, or see your account balance. Yet you want the bank to confirm that you didn’t overdraw, that you have enough funds, and that the operation is valid.
In this scenario, you:
- Use your calculator and spreadsheet at home to calculate the transfer;
- Generate a mathematical “receipt” (STARK proof) stating “I followed the rules, didn’t spend extra money, and didn’t fake anything”;
- Send the receipt to the bank instead of sending the bill;
- The bank only examines the “receipt,” verifies mathematically that what you’re saying is true, and approves the transfer;
- The bank doesn’t know exactly what you transferred, only that “this transaction is valid.”
In Miden:
- “You” are the user’s client;
- The “calculator” is the Miden VM;
- The “mathematical receipt” is the STARK proof;
- The “bank” is the Miden Verifier on Ethereum;
- “Whether you have money” or “whether you violated rules” are all computed locally and proven mathematically to convince the network;
- The entire process doesn’t require revealing specific details or having others re-run your program.
This “prove, don’t disclose” approach is the essence of Zero-Knowledge.
Summary
Miden doesn’t treat ZK as an add-on component but deeply integrates it into every instruction execution in the VM. Through the Trace → AIR → STARK proof pipeline, Miden has achieved a blockchain execution model that truly offers local execution, on-chain verification, and zero privacy leakage, pioneering application-layer virtual machines based on STARK.
5. Miden Development Experience and Tools Overview

Summary of Miden development experience and tools (Source: Gate Learn creator Max)
Miden’s development experience is specifically designed for ZK applications, combining the advantages of modularity, type safety, and local execution, allowing developers to both flexibly build systems and securely deploy to the blockchain.
6. Typical Applications and Use Cases: What Miden Can Do That Other Chains Cannot
6.1 “Order Matching No Longer On-Chain” — The Next Step for DeFi
Building an order book-style DEX on traditional chains means every buy and sell match needs to be written to the block. This is not only expensive and has high latency, but is also vulnerable to frontrunning (MEV) exploitation.
How does Miden do it?
- Matching occurs on the client side (mobile/server);
- Users package a batch of transactions, generating a ZK proof;
- The network only verifies “these transactions are valid”, without requiring each transaction to be on-chain;
- All transaction details are hidden from outside view, only the results update the state.
Result: Transactions are fast, fees are low, no MEV, making high-frequency trading and on-chain market making a reality.
6.2 Wallets Are No Longer Just Addresses, But Smart “Identity Terminals”
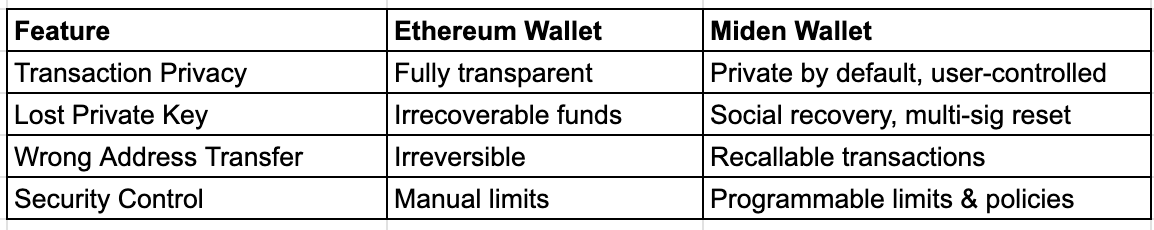
Comparison between EVM wallets and Miden wallets (Source: Gate Learn creator Max)
In Miden, each account is a smart contract, transforming “wallets” into identity terminals with definable rules. The user experience is similar to banking apps, while maintaining on-chain self-custody advantages.
6.3 Why Must Game Item Properties Be Visible to Everyone?
Game scenario example:
In an on-chain MMORPG, you mine a “rare sword” with hidden attributes, but once on-chain, others know it has bonuses, is valuable, and could target you.
How Miden solves this:
- Game logic and attributes execute locally;
- Attribute bonuses, cooldown times, skills, etc. are hidden as private states locally;
- Through ZK proofs, you tell the main chain “this sword defeated the monster” without exposing the sword’s attributes;
- Other players only know you won, not what you used.
This enables truly fair yet confidential gaming experiences, allowing Web3 games to finally achieve non-spoiler and anti-cheat capabilities.
6.4 Private Payments ≠ Non-Compliant
On Ethereum: Paying 1 ETH to someone = telling the world who you paid, when, and how much.
On Miden:
- You can set transactions to be visible only to “trusted verifiers”;
- Regulatory bodies can verify transactions exist and comply with regulations, without reconstructing the entire picture;
- This enables a payment system that is “provably private + audit-ready + user-controlled”.
Typical applications include DAO treasury management, multinational corporate payments, on-chain salaries, and Web3 banking.
6.5 New Paradigm: Off-Chain AI + On-Chain Proof
Miden allows you to run an AI model locally (like market price prediction, medical advice) and then submit the results to the blockchain through STARK proofs.
Example flow:
- Model runs locally;
- Users generate ZK proof: “This is the result produced by the model based on a certain dataset”;
- The main chain only verifies “execution is valid”, without knowing the process or input.
This enables applications to build trusted on-chain interactions while preserving model intellectual property and user privacy. Examples include medical AI, risk control models, and enterprise decision logic, all of which can achieve “black box verification”.
6.6 Summary
Miden is not just an accelerator or privacy extension layer; it represents an entirely new paradigm: from “on-chain ledger” to “on-chain trusted computing system”. Miden enables developers to build truly secure, composable, auditable yet opaque Web3 applications.
7. Challenges and Prospects
Despite Miden demonstrating enormous potential in zero-knowledge technology for scalability, privacy, and development paradigms, as an emerging architecture, it still faces a series of challenges.
- The developer ecosystem is still in its early stages. Compared to the mature EVM ecosystem, Miden’s toolchain, language support, and component libraries are still being improved. Although Rust compilation support is under development, most smart contracts still need to be written in MASM, creating a certain barrier for non-low-level developers.
- While STARK proofs are transparent and efficient, they still generate relatively large volumes, which places higher demands on mobile devices or bandwidth-limited users. Although this can be alleviated in the future through proof aggregation, dedicated proving services, and other methods, it remains one of the usability bottlenecks in the short term.
- Tension between privacy and compliance still exists. Although Miden provides a flexible “verifiable but opaque” mechanism, the complexity of regulatory environments may impose restrictions on certain application patterns. Developers need to provide auditability, controllability, and security while building privacy-protecting systems to achieve a balance with realistic compliance frameworks.
Looking ahead, Miden’s development roadmap is clear and well-defined. With the maturation of the Rust toolchain, the expansion of development templates and component ecosystems, and integration with the Polygon AggLayer mainnet, it has the potential to become the default runtime for Web3 applications—especially for scenarios requiring high-complexity logic, strong privacy controls, and minimal on-chain footprint. The “client-side proving + on-chain verification” paradigm opened by Miden may be the key channel for truly scaling on-chain computation.

Miden Development Roadmap (Source: Miden Official Documentation)
8. Conclusion
Miden is not a minor modification to traditional blockchain architecture, but a complete reconstruction. With zero-knowledge proofs at its core, it pushes transaction execution and state management to the client side, leaving the network to handle only verification and consensus. This way, performance, privacy, and security are no longer compromising options but can be achieved simultaneously.
Through Miden, developers can build more complex, private, and flexible applications, while users gain greater control and security. It not only expands the technical boundaries of blockchain but also opens up new imaginative spaces for Web3 applications. As the ecosystem gradually improves, Miden has the potential to become a core component of the next generation of Web3 infrastructure. The future direction of blockchain development may lie within this paradigm of “on-chain trusted verification + off-chain free execution.”
Поділіться
Контент
1. Introduction
2. Introduction to Miden
3. Detailed Analysis of Miden VM Architecture
4. Miden’s Proof System: STARK-Powered Verifiable Execution Engine
5. Miden Development Experience and Tools Overview
6. Typical Applications and Use Cases: What Miden Can Do That Other Chains Cannot
7. Challenges and Prospects
8. Conclusion
Deep Analysis of Miden: A High-Performance Zero-Knowledge Virtual Machine Architecture Based on STARK
1. Introduction
2. Introduction to Miden
3. Detailed Analysis of Miden VM Architecture
4. Miden’s Proof System: STARK-Powered Verifiable Execution Engine
5. Miden Development Experience and Tools Overview
6. Typical Applications and Use Cases: What Miden Can Do That Other Chains Cannot
7. Challenges and Prospects
8. Conclusion
1. Introduction
With the continuous deepening of blockchain applications at scale, privacy protection and scalability have become core challenges urgently awaiting solutions across the industry. The emergence of Zero-Knowledge Proof (ZKP) technology provides a feasible path to address both simultaneously. As Ethereum co-founder Vitalik Buterin stated, “Highly efficient zero-knowledge proofs (ZK-SNARKs) can reveal enough information to prove our credibility while protecting our identity privacy” . In a recent blog post titled 《Why I support privacy》, he further pointed out: “Supporting privacy for everyone, and making the necessary tools open-source, universal, reliable, and secure, is one of the important challenges of our time.”
Privacy is not only a personal right but also the cornerstone of decentralization and censorship resistance. Meanwhile, ZK-Rollup, as a leader in Layer 2 solutions, is rapidly evolving, from early solutions focused on scalability like zkSync and Optimism, all the way to today’s zkEVM, constantly seeking balance between performance and compatibility. Miden has emerged against this background as a brand-new solution—it not only leverages the efficiency of STARK (Scalable Transparent ARguments of Knowledge: a zero-knowledge proof technology that allows others to quickly and confidently verify results without revealing computational details, with strong security, quantum resistance, and no need for any “trusted third party”. The efficiency of the proof system further pushes execution and state to the user side, redefining the concept of “composable privacy Rollup”.
2. Introduction to Miden

Source: https://x.com/0xMiden
Miden was incubated by Polygon Labs and became the independent 0xMiden project in spring 2025, positioning itself as an “Edge Blockchain”. Unlike traditional Rollups that require all transactions to be executed on-chain, Miden migrates most of the computation and proof generation processes to client devices, then submits compact STARK proofs to the network for verification. Polygon’s official blog states: “Miden will continue to evolve into a zero-knowledge driven ‘edge’ blockchain that moves execution and state to the client. Unlike traditional chains such as Sui, Aptos, and Solana, Miden unlocks a new design space for deploying scalable, privacy-friendly applications. After pushing state and execution down to user devices, developers can build powerful systems with complex logic and hybrid public-private states while maintaining user confidentiality and compliance.”

Source: Polygon Official Blog
Miden’s core advantages are reflected in the following aspects:
- High throughput and parallel execution: Inspired by the Actor model, each account (Actor) independently executes and generates proofs, eliminating global lock contention and greatly improving parallelism and throughput.
- Privacy-first with optional disclosure: Default private ledger only stores state commitments, with the option to selectively disclose specific transactions or contract calls when necessary, enabling flexible privacy strategies.
- Client-side local proving: Leveraging STARK’s transparency and efficiency, client devices can complete proof generation for complex transactions within 1-2 seconds. As of May 6, 2025 Beijing time, the cost of generating common proofs on mainstream MacBook Pro is approximately 90K cycles.
- Compatible with Ethereum security: Miden Rollup’s AggLayer is tightly integrated with the Ethereum mainnet, inheriting its strong security guarantees and decentralized characteristics.
Specifically, the Polygon Miden website states: “With Polygon Miden, developers can build novel high-throughput, privacy-friendly applications spanning payments, DeFi, digital assets, and gaming, with applications and users securely anchored to Ethereum and AggLayer” . To date, Miden has completed open-sourcing its VM, released its developer SDK, and entered the Alpha testnet v6 phase, drawing ever closer to its mainnet launch target in the fourth quarter of 2025.
In summary, by combining “client-side execution + ZK proofs + edge architecture,” Miden not only provides a new paradigm for quantifiable privacy and unlimited scalability but also lays the technological foundation for the next generation of Web3 infrastructure. Next, we will delve deeper into its VM architecture and proof system.
3. Detailed Analysis of Miden VM Architecture
Miden VM is a Turing-complete virtual machine specifically designed for efficient zero-knowledge proofs, with its core objective being the local execution of smart contract logic on client devices and generation of STARK proofs that can be quickly verified on-chain. The following four sub-sections provide an in-depth analysis of its architectural composition and execution process.
3.1 Stack-based Virtual Machine and Instruction Set
Stack-based Execution Model
Miden VM adopts a stack machine architecture, where all instruction inputs and outputs are processed through an operation stack. This design greatly simplifies state representation during proof generation, as only stack read/write operations need to be recorded, without maintaining complex register states.RISC-like Minimal Instruction Set
The virtual machine instruction set is kept deliberately simple—similar to a Reduced Instruction Set Computer (RISC)—to minimize the number of provable constraints. For example, arithmetic operations, logical operations, stack operations, and control flow instructions are broken down into the most basic micro-ops, with each instruction mapped to finite field arithmetic relations during proof generation. Miden VM efficiently transforms the execution of each instruction into algebraic constraints, generating and verifying them through STARK, with proof size loosely coupled to program complexity.
3.2 Program Memory Organization
During execution, the program state in Miden VM is distributed across the following logical segments:

Miden VM Memory Segment Responsibility Table (Source: Gate Learn Creator Max)
This multi-segment memory model not only facilitates different data access patterns but also helps independently constrain each segment during proof construction, optimizing lookups and parallelism.
3.3 Execution Flow and Proof Generation

Miden VM Architecture Diagram (Source: Gate Learn Creator Max)
Loading and Initialization
The client loads contract bytecode into the Code Segment, prepares the execution context, and obtains necessary Advice Tape inputs from the blockchain or side channel; it also loads the initial state commitment of an account or note.Trace Table Construction
During execution, the VM sequentially records a “Trace Table”—a multi-column table where each column represents the evolution of memory segments or stack top positions over time.AIR Transformation
The Trace Table is converted into an Algebraic Intermediate Representation (AIR), encoding all consistency conditions for VM behavior (such as stack pointer increments/decrements, instruction semantics) as polynomial constraints.STARK Proof
The Prover generates a STARK proof for the AIR. Due to STARK’s transparency (no trusted setup required) and efficiency, the client only needs O(N log N) time to process thousands of instruction-level Traces.Verifier Validation
The verifier only needs to check submitted polynomial evaluations and low-dimensional sampling, with complexity at the polynomial level of the proof size, typically completing within tens of milliseconds, greatly improving on-chain throughput.
The entire execution and proof generation process takes approximately 1-2 seconds (about 90K VM cycles) on the Miden client, while on-chain verification is even faster, enabling large-scale parallel transaction validation.
3.4 Parallelism and Composability
Actor Model
Miden VM treats each account (or note) as an independent Actor, with execution and state updates completely decoupled. This allows multiple transaction scripts to execute in parallel on the client, generate proofs in parallel, and then be submitted in batches for network aggregated validation. The Actor model combined with zero-knowledge proofs lets users prove state transitions locally, which are then aggregated in parallel by the network, significantly increasing throughput.Composable Scripts
Through Foreign Procedure Invocation (FPI), one contract script can call another contract’s “read-only” procedure without interrupting the local proof process. FPI essentially incorporates cross-contract read-only call state operations into the same Trace Table, achieving efficient composition.
3.5 Simple Explanation: What is Miden VM Like?
You can imagine Miden VM as a “privacy computing micro-factory” that executes tasks locally on your smartphone and produces an officially certified “work record” that can be sent to the main network for verification.
Example:
Suppose you’re using an on-chain RPG game where you buy a piece of land and then build a castle using game coins.
In traditional smart contracts: All your operations (position, fund flow, building actions) must be executed on-chain, with information completely public, both wasting block space and compromising privacy.
Using Miden VM:
- All logic—“Do I have enough coins? Am I in the correct position? Do I comply with building rules?”—is executed locally on your phone;
- Then Miden VM generates a mathematical proof (STARK proof) on your phone, telling the network: “This user definitely followed the rules”;
- The blockchain doesn’t need to know how you built it, it only verifies the proof is correct and updates the state.
The benefits of this design are:
- The network doesn’t need to execute every transaction, only verify proofs, saving resources;
- User operations can remain completely private, with selective disclosure only when needed;
- Multiple players can execute their own logic and generate their own proofs simultaneously, with extremely high parallelism, without competing for on-chain resources.
In conclusion, the key to Miden VM’s architecture lies in simplified provable instructions, multi-segment memory separation, efficient Air→STARK pipeline, and the Actor parallel model, ensuring that complex logic can be easily expressed on client devices while proof verification can be completed on-chain at extremely low cost, providing a solid foundation for the next generation of high-performance, privacy-friendly ZK-Rollup applications.
4. Miden’s Proof System: STARK-Powered Verifiable Execution Engine

Miden proof system diagram (Source: Gate Learn creator Max)
In Miden, zero-knowledge proofs aren’t just an “add-on module,” but the core operating mechanism of the entire protocol. Miden is built on the STARK (Scalable Transparent ARguments of Knowledge) system, designed from the ground up for “local execution + zero-knowledge proofs.” This section will deeply analyze Miden’s proof process and its underlying mathematical mechanisms, explaining why STARK is its preferred choice.
4.1 Why Choose STARK Instead of SNARK?
Compared to SNARK technology widely used in projects like zkEVM, Miden chose STARK technology for three key reasons:
No Trusted Setup Required (Transparent)
STARK uses hash functions (such as Rescue, Blake3, etc.) rather than elliptic curve cryptography, eliminating dependence on trusted initial parameters. This removes the centralization risks that come with “multi-party computation (MPC) trusted setup failures.”Quantum Attack Resistance
STARK is based on hash security, making it more robust against future quantum computing threats.Fast Proof Generation, Efficient Verification
Although STARK proofs are slightly larger than SNARK proofs, they verify faster, making them more suitable for large-scale parallel verification on-chain.
The research team at Polygon Labs states:
“Miden chose STARK not to be compatible with old paradigms, but to design an entirely new system that maximizes scalability and security.”
4.2 Trace Table and Execution Trajectory
In traditional computing, we can record every step of program execution, such as each variable assignment or function call. In Miden VM, these operations are transformed into an execution trace—a table called the Trace Table that contains snapshots of the program’s state at each step in the time dimension.
Each column in the Trace Table represents the evolution of a register, memory unit, or stack value;
Each row represents a moment (cycle) in the program’s execution.
For example:

Every Miden instruction can be precisely recorded and converted into constraints for the next stage of proof construction.
4.3 AIR (Algebraic Intermediate Representation)
After constructing the Trace Table, the next step is converting it to AIR (Algebraic Intermediate Representation). This is a method of representing program semantics as polynomial constraints, with core ideas including:
- Each rule, such as “the stack top after addition equals the sum of two numbers,” can be expressed as: “stack[0]_next = stack[0]_curr + stack[1]_curr”
- All rules are verified in a finite field, ensuring the STARK system can efficiently generate proofs.
- Low Degree Extension (LDE) technology is used to extend discrete data into continuous functions, making deceptive modifications detectable through probabilistic testing.
Through AIR, Miden can encode the claim “the execution is valid” as a mathematically verifiable statement.
4.4 STARK Proof Process
The complete STARK proof generation includes the following steps:
- Prover builds execution trace: Generates a Trace Table based on the smart contract logic executed locally by the user;
- Conversion to AIR system: Maps each instruction to algebraic constraints;
- Low-degree extension and commitment: Commits to the extended data through mechanisms like Merkle Trees;
- FRI protocol: Verifies the low-degree property of polynomials, ensuring the trace is valid;
- Proof output: Generates a proof of approximately 30-100KB, which the user submits to the network.
This entire process is completed on the client side, typically taking only 1-2 seconds, and can even run on mobile devices (or be delegated to external prover services if performance is insufficient).
4.5 On-Chain Verification and State Updates
Miden’s on-chain Verifier contract (inherited from Ethereum) performs the following operations on received STARK proofs:
- Quickly validates whether the AIR holds (through sampling verification);
- Checks if public inputs (such as state commitments, block height) match;
- Updates the global state (such as account storage trees, Nullifiers);
- Registers new states or consumes states of notes.
Thanks to STARK’s transparency and parallelism, the Verifier can simultaneously verify proofs of thousands of transactions, greatly increasing throughput and reducing on-chain load.
4.6 Simple Explanation: Miden’s STARK Proof System is Like a “Mathematical Receipt”
You can think of Miden’s zero-knowledge proof process as a “paperless banking transaction”:
Metaphorical scenario:
Imagine you’re making a bank transfer, but you don’t want the bank to know how much money you transferred, to whom, or see your account balance. Yet you want the bank to confirm that you didn’t overdraw, that you have enough funds, and that the operation is valid.
In this scenario, you:
- Use your calculator and spreadsheet at home to calculate the transfer;
- Generate a mathematical “receipt” (STARK proof) stating “I followed the rules, didn’t spend extra money, and didn’t fake anything”;
- Send the receipt to the bank instead of sending the bill;
- The bank only examines the “receipt,” verifies mathematically that what you’re saying is true, and approves the transfer;
- The bank doesn’t know exactly what you transferred, only that “this transaction is valid.”
In Miden:
- “You” are the user’s client;
- The “calculator” is the Miden VM;
- The “mathematical receipt” is the STARK proof;
- The “bank” is the Miden Verifier on Ethereum;
- “Whether you have money” or “whether you violated rules” are all computed locally and proven mathematically to convince the network;
- The entire process doesn’t require revealing specific details or having others re-run your program.
This “prove, don’t disclose” approach is the essence of Zero-Knowledge.
Summary
Miden doesn’t treat ZK as an add-on component but deeply integrates it into every instruction execution in the VM. Through the Trace → AIR → STARK proof pipeline, Miden has achieved a blockchain execution model that truly offers local execution, on-chain verification, and zero privacy leakage, pioneering application-layer virtual machines based on STARK.
5. Miden Development Experience and Tools Overview

Summary of Miden development experience and tools (Source: Gate Learn creator Max)
Miden’s development experience is specifically designed for ZK applications, combining the advantages of modularity, type safety, and local execution, allowing developers to both flexibly build systems and securely deploy to the blockchain.
6. Typical Applications and Use Cases: What Miden Can Do That Other Chains Cannot
6.1 “Order Matching No Longer On-Chain” — The Next Step for DeFi
Building an order book-style DEX on traditional chains means every buy and sell match needs to be written to the block. This is not only expensive and has high latency, but is also vulnerable to frontrunning (MEV) exploitation.
How does Miden do it?
- Matching occurs on the client side (mobile/server);
- Users package a batch of transactions, generating a ZK proof;
- The network only verifies “these transactions are valid”, without requiring each transaction to be on-chain;
- All transaction details are hidden from outside view, only the results update the state.
Result: Transactions are fast, fees are low, no MEV, making high-frequency trading and on-chain market making a reality.
6.2 Wallets Are No Longer Just Addresses, But Smart “Identity Terminals”

Comparison between EVM wallets and Miden wallets (Source: Gate Learn creator Max)
In Miden, each account is a smart contract, transforming “wallets” into identity terminals with definable rules. The user experience is similar to banking apps, while maintaining on-chain self-custody advantages.
6.3 Why Must Game Item Properties Be Visible to Everyone?
Game scenario example:
In an on-chain MMORPG, you mine a “rare sword” with hidden attributes, but once on-chain, others know it has bonuses, is valuable, and could target you.
How Miden solves this:
- Game logic and attributes execute locally;
- Attribute bonuses, cooldown times, skills, etc. are hidden as private states locally;
- Through ZK proofs, you tell the main chain “this sword defeated the monster” without exposing the sword’s attributes;
- Other players only know you won, not what you used.
This enables truly fair yet confidential gaming experiences, allowing Web3 games to finally achieve non-spoiler and anti-cheat capabilities.
6.4 Private Payments ≠ Non-Compliant
On Ethereum: Paying 1 ETH to someone = telling the world who you paid, when, and how much.
On Miden:
- You can set transactions to be visible only to “trusted verifiers”;
- Regulatory bodies can verify transactions exist and comply with regulations, without reconstructing the entire picture;
- This enables a payment system that is “provably private + audit-ready + user-controlled”.
Typical applications include DAO treasury management, multinational corporate payments, on-chain salaries, and Web3 banking.
6.5 New Paradigm: Off-Chain AI + On-Chain Proof
Miden allows you to run an AI model locally (like market price prediction, medical advice) and then submit the results to the blockchain through STARK proofs.
Example flow:
- Model runs locally;
- Users generate ZK proof: “This is the result produced by the model based on a certain dataset”;
- The main chain only verifies “execution is valid”, without knowing the process or input.
This enables applications to build trusted on-chain interactions while preserving model intellectual property and user privacy. Examples include medical AI, risk control models, and enterprise decision logic, all of which can achieve “black box verification”.
6.6 Summary
Miden is not just an accelerator or privacy extension layer; it represents an entirely new paradigm: from “on-chain ledger” to “on-chain trusted computing system”. Miden enables developers to build truly secure, composable, auditable yet opaque Web3 applications.
7. Challenges and Prospects
Despite Miden demonstrating enormous potential in zero-knowledge technology for scalability, privacy, and development paradigms, as an emerging architecture, it still faces a series of challenges.
- The developer ecosystem is still in its early stages. Compared to the mature EVM ecosystem, Miden’s toolchain, language support, and component libraries are still being improved. Although Rust compilation support is under development, most smart contracts still need to be written in MASM, creating a certain barrier for non-low-level developers.
- While STARK proofs are transparent and efficient, they still generate relatively large volumes, which places higher demands on mobile devices or bandwidth-limited users. Although this can be alleviated in the future through proof aggregation, dedicated proving services, and other methods, it remains one of the usability bottlenecks in the short term.
- Tension between privacy and compliance still exists. Although Miden provides a flexible “verifiable but opaque” mechanism, the complexity of regulatory environments may impose restrictions on certain application patterns. Developers need to provide auditability, controllability, and security while building privacy-protecting systems to achieve a balance with realistic compliance frameworks.
Looking ahead, Miden’s development roadmap is clear and well-defined. With the maturation of the Rust toolchain, the expansion of development templates and component ecosystems, and integration with the Polygon AggLayer mainnet, it has the potential to become the default runtime for Web3 applications—especially for scenarios requiring high-complexity logic, strong privacy controls, and minimal on-chain footprint. The “client-side proving + on-chain verification” paradigm opened by Miden may be the key channel for truly scaling on-chain computation.

Miden Development Roadmap (Source: Miden Official Documentation)
8. Conclusion
Miden is not a minor modification to traditional blockchain architecture, but a complete reconstruction. With zero-knowledge proofs at its core, it pushes transaction execution and state management to the client side, leaving the network to handle only verification and consensus. This way, performance, privacy, and security are no longer compromising options but can be achieved simultaneously.
Through Miden, developers can build more complex, private, and flexible applications, while users gain greater control and security. It not only expands the technical boundaries of blockchain but also opens up new imaginative spaces for Web3 applications. As the ecosystem gradually improves, Miden has the potential to become a core component of the next generation of Web3 infrastructure. The future direction of blockchain development may lie within this paradigm of “on-chain trusted verification + off-chain free execution.”


